All the world is now at our finger tips, thanks to the telecommunication revolution! Know about the latest technologies in Telecommunication industry, through the telecomblog!
Monday, December 31, 2007
Triple Play Networks
Technological advances
Technology has evolved from dedicated networks for different kinds of services to converged IP-based infrastructures that can transmit data, voice and video over a single pipe, in real time, to thousands of users. The challenge lies in managing these conflicting demands reliably and efficiently, at acceptable cost, while providing the consumer with the quality of experience he has come to expect. Multi-play is the provision of different telecommunication services, such as Broadband Internet access, television, telephone, and mobile phone service, by organizations that traditionally only offered one or two of these services. Multi-play is a catch-all phrase; usually, the terms triple play or quadruple play are used to describe a more specific meaning.
No matter how advanced the technology may become,CRM is the most important factor in the success of any triple-play network. Home users who subscribe to triple-play networks have the advantage that they have to pay only one bill each month . The ideal triple-play system functions 24 hours a day, 7 days a week. Non-technical features such as these are crucial to maintaining customer loyalty.
Regulation
There are multiple and intense regulatory battles over triple play services as the cable and telecom service providers attempt to keep out new competitors. Both industries have been regulated monopolies, and regulatory capture has long been a core competency for them. Prices and terms of service are also of top priority. Cable providers want to compete with telecom companies for local voice service, but want to keep them from competing with cable ops for television service. Whereas , telecom providers want to deliver television service but want to block competition for voice service from cable operators. Both industries cloak their demands for favorable regulatory treatment in claims that their positions favor the public interests. In March 2007 cable operators scored a major victory when the FCC overruled two state public service commissions by ruling that incumbent local exchange carriers must connect to VoIP services. In the other direction, also in March 2007 the FCC limited the powers of municipalities and states over telecom service providers that want to compete with cable TV companies. All three Republican members of the FCC voted for this decision, while both Democratic members voted against it and one predicted either Congress or the courts would overturn it.
Challenges
Today’s world is digital and dynamic. The global market for integrated consumer devices and triple play services is growing explosively: in 2005, online gaming revenue increased by 43% (DFC Intelligence), while VoIP and broadband video grew by 63% and more than 100% year-over-year respectively . NEMs, telcos and cable operators must validate their products under real-world conditions to be confident that they are able to handle complex voice, video and data services, in real time, securely, for large user populations. The challenges in offering triple play are mostly associated with determining the right business model, backend processes, customer care support and economic environment rather than technology. But that does in no way lesser the importance of technical challenges present in the deployment of the network.
Some of the more challenging issues facing service providers can be broken down as follows:
• How to ensure individual service quality and priority, especially quality-sensitive voice and
video services
• How to provision the unique requirements of each service; specifically, video and voice require high QoS and significant user interaction, data is simply an “always on” state
• How to integrate new customer-located triple play devices like set-top boxes and voice-over-IP (VoIP) phone systems with existing systems
• How to manage and support the individual services once they are provisioned.
Thursday, November 15, 2007
Chaos.. every where
without any errors at all. Numerous ways to achieve this task have been devised in the past
by man and the quest for better technologies continues. The latest one is to utilize the
chaotic laws of nature! i.e. bringing order out of chaos!!
Chaos.. every where
The seemingly random nature of the chaotic phenomenon was thought about, out of curiosity in
early days. Bringing in order out of chaos was never ever thought of by man. But as the technology improves, researchers are looking to bring out just this. The results are said to
be very encouraging. Under favourable conditions, initial tests were able to achieve giga-bit speeds over a few hundred kilometers.
Bringing order...

A unique feature of the chaotic system is that, even though they have a seemingly chaotic
nature as a whole, the immediate behavior is somewhat predictable. So this means, the near-term behaviour of the system can be made controllable. A simplest example uses the
Lorenz Attractor. As said above, by making a few changes inn the Lorenz system equations,the
system trace can be sent to one of the 'butter-fly wings'. If we consider one wing or lobe as '0' and the other as '1', the result is a very robust digital system! A receiver needs only to synchronize with the transmitter to receive the message.
The biggest advantage of such systems is that it is much more easier to to generate these chaotic signals. They are found to be robust than the conventional ones. It has been reported that the systems are difficult to crack into, due to the chaotic nature of the signal itself. It can be easily confused with the random noise. Add to it any common cryptographic technology, you get a very secure communication system.
The future may be resting on this still evolving phenomenon. Researchers have not fully understood the chaotic laws as on today. A better understanding could make way to a totally
secure, but chaotic way of communication!!
Tuesday, October 30, 2007
Coding theory in communication systems
Introduction
Different types of codes are used to encode digital data before transmission through noisy or error-prone channels. At the receiver, the bitstream is to be decoded to recover the original data, correcting errors in the process. The purpose is to improve the capacity of a channel by blending a few carefully designed redundant information to the data being transmitted through the channel, which is commonly known as channel coding. Convolutional coding and block coding are the two major forms of channel coding. When Convolutional codes operate on serial data,the Block codes operate on relatively large blocks of data. The optimum decoding method is maximum-likelihood decoding where the decoder attempts to find the closest "valid" sequence to the received bitstream. The Viterbi Algorithm does just that!
Viterbi algorithm
Convolutional encoding with Viterbi decoding is a Forward Error Correction technique that is particularly suited to a channel in which the transmitted signal is corrupted mainly by additive white gaussian noise (AWGN). Viterbi decoding was developed by Andrew J. Viterbi, a founder of Qualcomm Corporation. Most recently, he has been concentrating his efforts on establishing CDMA as the multiple access technology of choice for cellular telephony and wireless data communication. His seminal paper on the technique is "Error Bounds for Convolutional Codes and an Asymptotically Optimum Decoding Algorithm," published in IEEE Transactions on Information Theory, Volume IT-13, pages 260-269, in April, 1967. Since then, other researchers have expanded on his work by finding good convolutional codes, exploring the performance limits of the technique, and varying decoder design parameters to optimize the implementation of the technique in hardware and software. The Viterbi decoding algorithm is also used in decoding trellis-coded modulation, the technique used in telephone-line modems to squeeze high ratios of bits-per-second to Hertz out of the limited-bandwidth analog telephone lines. Currently,this application of the algorithm forms an integral part of the majority of wireless telecommunication systems, incorporated in both satellite digital television receivers and even your cellular mobile handsets.
Viterbi decoder implementations
For relatively small values of k, the Viterbi algorithm provides maximum likelihood performance and is highly parallelizable. Viterbi decoders are easy to implement in VLSI hardware and in software on CPUs with SIMD instruction sets. As mentioned earlier,at the receiver, the bitstream is to be decoded to recover the original data. The possible received bit sequences form a "trellis" structure and the Viterbi Algorithm tracks likely paths through the trellis before choosing the most likely path. The "trellis diagram" gives the receiver an idea about decoding. If a received sequence doesn't fit this graph, then it was received with errors, and the decoder must choose the nearest correct (fitting the graph) sequence. The real decoding algorithms exploit this idea. Convolutional codes are usually described using two parameters: the code rate and the constraint length. The code rate, k/n, is expressed as a ratio of the number of bits into the convolutional encoder (k) to the number of channel symbols output by the convolutional encoder (n) in a given encoder cycle. The constraint length parameter, K, denotes the "length" of the convolutional encoder, i.e. how many k-bit stages are available to feed the combinatorial logic that produces the output symbols. Closely related to K is the parameter m, which indicates how many encoder cycles an input bit is retained and used for encoding after it first appears at the input to the convolutional encoder. The m parameter can be thought of as the memory length of the encoder. A convolutional encoder is a discrete LTI - system. Every output of an encoder can be described by its own transfer function, which is closely related to a generator polynomial.
Turbo Codes: replacing Convolutional Codes
As stated earlier, newer and improved methods have been devised by researchers all over the world for convolutional-decoding. Turbo codes are one such set. These are a new class of iterated short convolutional codes that closely approach the theoretical limits imposed by Shannon's theorem with much less decoding complexity than the Viterbi algorithm on the long convolutional codes that would be required for the same performance. Turbo codes have not yet been concatenated with solid (low complexity) Reed-Solomon error correction codes. However, in the interest of planetary exploration this may someday be done. The future and the past The convolutional coding/decoding was considered hopelessly complex in 1967 when it was published by Viterbi. But the algorithm survived the test of times, starting from a huge rack of equipment in the 70s' to a fraction of a tiny chip today. Convolutional codes with Viterbi decoding first used in spacecrafts and military satellites in the early 70s ultimately became the backbone of commercial voice and data ommunication satellites and direct broadcast satellites, residing in tens of millions of receivers today. The reach is counted in billions today! Truly it has been a journey through hardships to the stars!
References
http://www.Wikipedia.org
http://home.netcom.com/~chip.f/viterbi/tutorial.html
IEEE SIGNAL PROCESSING MAGAZINE JULY 2006
Wednesday, September 26, 2007
Wireless Packet Sniffers
The packet sniffers can be used to:
- Analyze network problems.
- Detect network intrusion attempts.
- Gain information for effecting a network intrusion.
- Monitor network usage.
- Gather and report network statistics.
- Filter suspect content from network traffic.
- Spy on other network users and collect sensitive information such as passwords (depending on any content encryption methods which may be in use)
- Reverse engineer protocols used over the network.
- Debug client/server communications.
- Debug network protocol implementations.
More and more wireless sniffer's are becoming available. The first question dealing with wireless sniffing is the signaling. This wireless standard uses "spread spectrum" technology. It allows many users to share the same spectrum like cellular. CDMA uses spread spectrum, where each "code" (code division multiplexing) determines the sequence used to "spread" the signal. So, in theory, spread-spectrum makes it impossible to eavesdrop. The eavesdropper would need to know the "spreading" function used.
Spread-spectrum technology came out of the cold war as a way of sending signals that were near impossible to eavesdrop on. The theory is that an eavesdroppper only hears whitenoise, and that even proving there is a signal could be difficult. However, it is assumed that we could securily communicate the "spreading function" to both the transmitter and receiver. This isn't reasonable in consumer-grade products that we'll be buying. The keys will be distributed manually. Moreover, there aren't that many keys. The upshot is that spread-spectrum has little impact as an anti-sniffing countermeasure. Data encryption in the communication will make sniffing difficult, but not impossible.
A few Sniffers available...
AirSnort is a wireless LAN (WLAN) tool which recovers encryption keys. AirSnort operates by passively monitoring transmissions, computing the encryption key when enough packets have been gathered.
Airosniff can be used to assist in the identification of wireless networks by sniffing SSIDs. Airosniff, for the Cisco Aironet card allows one to seek out wireless networks, auto-config the card for sniffing and perform access point vendor identification.
Ethereal is a GUI sniffer which understands 802.11b frames. Unfortunately right now the only way to get wireless frames into Ethereal is to use Linux 2.4.6 (or custom patches to 2.2.19) or the latest bleeding edge FreeBSD and patches to Libpcap and BPF.
Wavemon is a text-mode wireless utility. It shows all the iwconfig info in a screen that refreshes itself. It also has a histogram of signal strength and a list of in-range APs.
Grasshopper is a handheld, wireless receiver designed specifically for sweeping and optimizing Local Area Networks. The instrument measures coverage of direct sequence CDMA networks which operate on the IEEE 802.11b standard allowing the user to measure and determine the AP (AccessPoint), PER (Packet Error Rate) and RSSI signal levels aiding in locating the hub and access points throughout a building. Grasshopper detects and differentiates from narrow-band multipath interferences such as microwave ovens and frequency hopping systems and features a built-in display, keypad and removable battery pack for true portability.
Thursday, August 30, 2007
Wireless Communication Equipment..
Aerocomm is one company to watch out for if you are looking for the fastest way to go wireless, since they seem to have a wide range of products. The company claims to offer compact transceivers, which are ready to integrate, and offers technology that ensures reliable communication even in frequency-polluted areas. The industrial and commercial range includes 2.4GHz/900MHz RF transceiver modules and the Zigbee transceiver module. The ZigBee transceiver (ZB2430) is an SoC compliant module. This is available in two versions to suit varying requirements. The ZB2430 and ZB2430-100 are two where the latter is offers an extended communication capability. The ZB2430 uses 2.4GHz ISM band, so OEMs looking for standardization can use it. The module comes as either full-function devices or reduced function devises.
Data Hunter offers an OEM WLAN serial server module, typically targeted at portable, low cost equipments. It supports the major network/protocol standards like TCP/IP, UDP/IP, HTTP, ARP, SNMP etc. It also uses the 2.4GHz band typically upto 2.48GHz. It has a very useful power-save mode, which is helpful in low-power applications. It is named 802.11b "Mini-b" module as given in their website.
Air-wave offers AWM630, a new range of wireless modules operating on again, the 2.4GHz ISM band. The company claims that the devices are FCC compliant, so a global market is the target. Typical applications for the AWM630 may be for professional or domestic sound/video transmissions, security systems, or public information systems. The video compatibility for both PAL and NTSC is present in the same module. A stereo audio is also supported. The AWM630 series is RoHS compliant, that is what the company claims. The prices are very competitive and the modules are available through saelig.
Conexant is another company which offers a single chip 802.11b WLAN compatible device for small, embedded portable applications. The company offers CX53113, a low power , small form factor module which is suitable for mobile applications. It also operates in the 2.4GHz ISM band, supporting data rates up and above 6Mbps.All the above products are targeted at different end-markets but have a lot of things in common. It is just a pointer as to where to look for if you are intending to cut cables from your application and intend to do it fast!!!
Monday, August 13, 2007
On WiMax Architecture
The IEEE only defined the Physical (PHY) and Media Access Control (MAC) layers in 802.16. This approach has worked well for technologies such as Ethernet and WiFi, which rely on other bodies such as the IETF (Internet Engineering Task Force) to set the standards for higher layer protocols such as TCP/IP, SIP, VoIP and IPSec. In the mobile wireless world, standards bodies such as 3GPP and 3GPP2 set standards over a wide range of interfaces and protocols because they require not only airlink interoperability, but also inter-vendor inter-network interoperability for roaming, multi-vendor access networks, and inter-company billing. Vendors and operators have recognized this issue, and have formed additional working groups to develop standard network reference models for open inter-network interfaces. Two of these are the WiMAX Forum’s Network Working Group, which is focused on creating higher-level networking specifications for fixed, nomadic, portable and mobile WiMAX systems beyond what is defined in the IEEE 802.16 standard, and Service Provider Working Group which helps write requirements and prioritizes them to help drive the work of Network WG.
The Mobile WiMAX End-to-End Network Architecture is based an All-IP platform, all packet technology with no legacy circuit telephony. It offers the advantage of reduced total cost of ownership during the lifecycle of a WiMAX network deployment. The use of All-IP means that a common network core can be used, without the need to maintain both packet and circuit core networks, with all the overhead that goes with it. A further benefit of All-IP is that it places the network on the performance growth curve of general purpose processors and computing devices, often termed “Moore’s Law”. Advances in computer processing occurs much faster than advances in telecommunications equipment because general purpose hardware is not limited to telecommunications equipment cycles, which tend to be long and cumbersome. The end result is a network that continually performs at ever higher capital and operational efficiency, and takes advantage of 3rd party developments from the Internet community. This results in lower cost, high scalability, and rapid deployment since the networking functionality is all primarily software-based services.In order to deploy successful and operational commercial systems, there is need for support beyond 802.16 (PHY/MAC) air interface specifications. Chief among them is the need to support a core set of networking functions as part of the overall End-to-End WiMAX system architecture.
Before delving into some of the details of the architecture, we first note a few basic tenets that have guided the WiMAX architecture development.
1. The architecture is based on a packet-switched framework, including native procedures based on the IEEE 802.16 standard and its amendments, appropriate IETF RFCs and Ethernet standards.
2. The architecture permits decoupling of access architecture (and supported topologies) from connectivity IP service. Network elements of the connectivity system are agnostic to the IEEE 802.16 radio specifics.
3. The architecture allows modularity and flexibility to accommodate a broad range of deployment options such as:·
Small-scale to large-scale (sparse to dense radio coverage and capacity) WiMAX networks·
· Urban, suburban, and rural radio propagation environments
· Licensed and/or licensed-exempt frequency bands
· Hierarchical, flat, or mesh topologies, and their variants
· Co-existence of fixed, nomadic, portable and mobile usage models
Support for Services and Applications
The end-to-end architecture includes the support for:
a) Voice, multimedia services and other mandated regulatory services such as emergency services and lawful interception,
b) Access to a variety of independent Application Service Provider (ASP) networks in an agnostic manner,
c) Mobile telephony communications using VoIP,
d) Support interfacing with various interworking and media gateways permitting delivery of incumbent/legacy services translated over IP (for example, SMS over IP, MMS, WAP) to WiMAX access networks and
e) Support delivery of IP Broadcast and Multicast services over WiMAX access networks.
Interworking and Roaming is another key strength of the End-to-End Network Architecture with support for a number of deployment scenarios. In particular, there will be support of
a) Loosely-coupled interworking with existing wireless networks such as 3GPP and 3GPP2 or existing wireline networks such as DSL and MSO, with the interworking interface(s) based on a standard IETF suite of protocols,
b) Global roaming across WiMAX operator networks, including support for credential reuse, consistent use of AAA for accounting and billing, and consolidated/common billing and settlement,
c) A variety of user authentication credential formats such as username/password, digital certificates, Subscriber Identify Module (SIM), Universal SIM (USIM), and Removable User Identify Module (RUIM).
The ASN represents a boundary for functional interoperability with WiMAX clients, WiMAX connectivity service functions and aggregation of functions embodied by different vendors. Mapping of functional entities to logical entities within ASNs as depicted in the NRM may be performed in different ways. The WiMAX Forum is in the process of network specifications in a manner that would allow a variety of vendor implementations that are interoperable and suited for a wide diversity of deployment requirements.Connectivity Service Network (CSN) is defined as a set of network functions that provide IP connectivity services to the WiMAX subscriber(s). A CSN may comprise network elements such as routers, AAA proxy/servers, user databases and Interworking gateway devices. A CSN may be deployed as part of a Greenfield WiMAX Network Service Provider (NSP) or as part of an incumbent WiMAX NSP.
The network specifications for WiMAX-based systems are based on several basic network architecture tenets, including those listed below.Some general tenets have guided the development of Mobile WiMAX Network Architecture and include the following:
a) Provision of logical separation between such procedures and IP addressing, routing and connectivity management procedures and protocols to enable use of the access architecture primitives in standalone and inter-working deployment scenarios,
b) Support for sharing of ASN(s) of a Network Access Provider (NAP) among multiple NSPs,
c) Support of a single NSP providing service over multiple ASN(s) – managed by one or more NAPs,
d) Support for the discovery and selection of accessible NSPs by an MS or SS,
e) Support of NAPs that employ one or more ASN topologies,
f) Support of access to incumbent operator services through internetworking functions as needed,
g) Specification of open and well-defined reference points between various groups of network functional entities (within an ASN, between ASNs, between an ASN and a CSN, and between CSNs), and in particular between an MS, ASN and CSN to enable multi-vendor interoperability,
h) Support for evolution paths between the various usage models subject to reasonable technical assumptions and constraints,
i) Enabling different vendor implementations based on different combinations of functional entities on physical network entities, as long as these implementations comply with the normative protocols and procedures across applicable reference points, as defined in the network specifications and
j) Support for the most trivial scenario of a single operator deploying an ASN together with a limited set of CSN functions, so that the operator can offer basic Internet access service without consideration for roaming or interworking.
The WIMAX architecture also allows both IP and Ethernet services, in a standard mobile IP compliant network. The flexibility and interoperability supported by the WiMAX network provides operators with a multi-vendor low cost implementation of a WiMAX network even with a mixed deployment of distributed and centralized ASN’s in the network. The WiMAX network has the following major features:Security The end-to-end WiMAX Network Architecture is based on a security framework that is agnostic to the operator type and ASN topology and applies consistently across Greenfield and internetworking deployment models and usage scenarios. In particular there is support for:
a) Strong mutual device authentication between an MS and the WiMAX network, based on the IEEE 802.16 security framework,
b) All commonly deployed authentication mechanisms and authentication in home and visited operator network scenarios based on a consistent and extensible authentication framework,
c) Data integrity, replay protection, confidentiality and non-repudiation using applicable key lengths,
d) Use of MS initiated/terminated security mechanisms such as Virtual Private Networks (VPNs),
e) Standard secure IP address management mechanisms between the MS/SS and its home or visited NSP.
Mobility and Handovers
The end-to-end WiMAX Network Architecture has extensive capability to support mobility and handovers. It will:
a) Include vertical or inter-technology handovers— e.g., to Wi-Fi, 3GPP, 3GPP2, DSL, or MSO – when such capability is enabled in multi-mode MS,
b) Support IPv4 or IPv6 based mobility management. Within this framework, and as applicable, the architecture SHALL accommodate MS with multiple IP addresses and simultaneous IPv4 and IPv6 connections,
c) Support roaming between NSPs,
d) Utilize mechanisms to support seamless handovers at up to vehicular speeds— satisfying well-defined (within WiMAX Forum) bounds of service disruption.
Some of the additional capabilities in support of mobility include the support of:
i) Dynamic and static home address configurations,
ii) Dynamic assignment of the Home Agent in the service provider network as a form of route optimization, as well as in the home IP network as a form of load balancing and
iii) Dynamic assignment of the Home Agent based on policies.Scalability, Extensibility, Coverage and Operator Selection
The end-to-end WiMAX Network Architecture has extensive support for scalable, extensible operation and flexibility in operator selection. In particular, it will:
a) enable a user to manually or automatically select from available NAPs and NSPs,
b) Enable ASN and CSN system designs that easily scale upward and downward – in terms of coverage, range or capacity,
c) Accommodate a variety of ASN topologies - including hub-and-spoke, hierarchical, and/or multi-hop interconnects,
d) Accommodate a variety of backhaul links, both wireline and wireless with different latency and throughput characteristics,
e) Support incremental infrastructure deployment,
f) Support phased introduction of IP services that in turn scale with increasing number of active users and concurrent IP services per user,
g) Support the integration of base stations of varying coverage and capacity - for example, pico, micro, and macro base stations and
h) Support flexible decomposition and integration of ASN functions in ASN network deployments in order to enable use of load balancing schemes for efficient use of radio spectrum and network resources.
Additional features pertaining to manageability and performance of WiMAX Network Architecture include:
a) Support a variety of online and offline client provisioning, enrollment, and management schemes based on open, broadly deployable, IP-based, industry standards,
b) Accommodation of Over-The-Air (OTA) services for MS terminal provisioning and software upgrades, and
c) Accommodation of use of header compression/suppression and/or payload compression for efficient use of the WiMAX radio resources.
References:-
--“Mobile WiMAX – Part II: Competitive Analysis”, WiMAX Forum, February, 2006
--Hassan Yagoobi, “Scalable OFDMA Physical Layer in IEEE 802.16 WirelessMAN”, Intel Technology Journal, Vol 08, August 2004.
-- Hassan Yagoobi, “Scalable OFDMA Physical Layer in IEEE 802.16 WirelessMAN”, Intel Technology Journal, Vol 08, August 2004.
-- G. Nair, J. Chou, T. Madejski, K. Perycz, P. Putzolu and J. Sydir, “IEEE 802.16 Medium Access Control and Service Provisioning”, Intel Technology Journal, vol 08, August 2004.
-- “Can WiMAX Address Your Applications?”, Westech on Behalf of the WiMAX Forum, October 24, 2005
Monday, July 30, 2007
UMA technology
Unlicensed Mobile Access (UMA) technology provides access to GSM and GPRS mobile services over unlicensed spectrum technologies, including Bluetooth and 802.11. By deploying UMA technology, service providers can enable subscribers to roam and handover between cellular networks and public and private unlicensed wireless networks using dual-mode mobile handsets. With UMA, subscribers receive a consistent user experience for their mobile voice and data services as they transition between networks.
In order to promote the widespread adoption of UMA technology, a number of leading companies within the wireless industry have jointly developed a set of open specifications. These specifications are available through this Web site, and may be used by vendors and carriers of wireless communications systems and applications to develop and deploy interoperable solutions.
In addition to developing and maintaining the initial specifications, the participating companies are actively working with the 3GPP standards organization to use the specifications as the basis for the development of a formal standard.
Highlights of UMA Technology:
- Seamless delivery of mobile voice and data services over unlicensed wireless networks.
- Provides the same mobile identity on Cellular RAN and unlicensed wireless networks.
- Seamless transitions (roaming and handover) between Cellular RAN and unlicensed wireless networks.
- Preserves investment in existing/future mobile core network infrastructure
- Independent of underlying unlicensed spectrum technology (e.g. WiFi™, Bluetooth™)
- Transparent to existing, standard CPE devices (e.g. access points, routers and modems)
- Utilizes standard “always on" broadband IP access networks (e.g. DSL, Cable, T1/E1, Broadband Wireless, FTTH…)
- Security equivalent to current GSM mobile networks
- No impact to operations of Cellular RAN (e.g. spectrum engineering, cell planning,…)
UMA Technology Architecture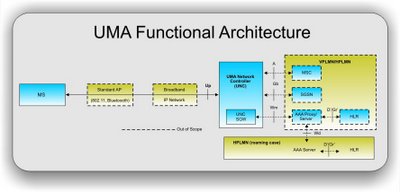
UMA Technology Operation
UMA technology provides alternative access to GSM and GPRS core network services via IP-based broadband connections. In order to deliver a seamless user experience, the specifications define a new network element (the UMA Network Controller, UNC) and associated protocols that provide for the secure transport of GSM/GPRS signalling and user plane traffic over IP. The UNC interfaces into the core network via existing 3GPP specified A/Gb interfaces.
How UMA Technology Works
- A mobile subscriber with a UMA-enabled, dual-mode handset moves within range of an unlicensed wireless network to which the handset is allowed to connect.
- Upon connecting, the handset contacts the UMA Network Controller (UNC) over the broadband IP access network to be authenticated and authorized to access GSM voice and GPRS data services via the unlicensed wireless network.
- If approved, the subscriber’s current location information stored in the core network is updated, and from that point on all mobile voice and data traffic is routed to the handset via the Unlicensed Mobile Access Network (UMAN) rather than the cellular radio access network (RAN).
- ROAMING: When a UMA-enabled subscriber moves outside the range of an unlicensed wireless network to which they are connected, the UNC and handset facilitate roaming back to the licensed outdoor network. This roaming process is completely transparent to the subscriber.
- HANDOVER: If a subscriber is on an active GSM voice call or GPRS data session when they come within range (or out of range) of an unlicensed wireless network, that voice call or data session can automatically handover between access networks with no discernable service interruption. Handovers are completely transparent to the subscriber.
UMA Interoperability
An open test specification is under development that can be used to facilitate interoperability testing between implementations. The test specification will be available through this web site. Companies planning to implement products based on the UMA specifications should seek bilateral compliancy testing agreements directly with other vendors.
In principle, the UMA specifications ensure interoperability similar to any other industry specifications, but the specifications may include options and parameters that have to be agreed bilaterally with other vendors. The UMA participating companies do not guarantee interoperability and the specifications may be upgraded without notice.